Windows senagent network traffic
This page was last modified 02:31, 10 May 2006.From Documentation
[edit]
Technical Note
Please note that this article recreates Technical Note 214, originally posted May 10, 2006.
[edit]
Senagent Network Traffic
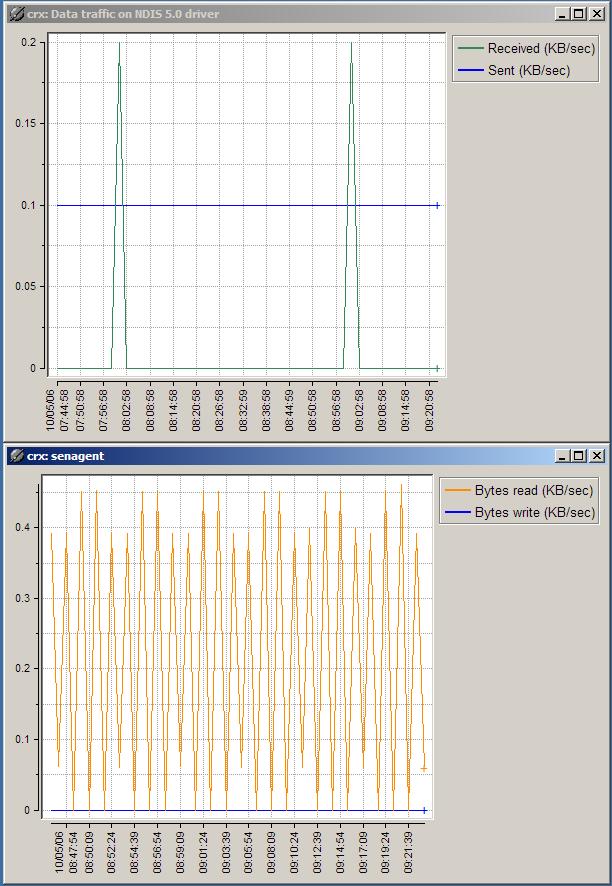
Tests were carried out to discover how much network traffic was generated by running Windows monitoring using the senagent executable file.
The test environment was a Linux machine for the Event Host, and a Windows2000 machine for the windows host. The windows machine was the only windows machine on the network, in order to maintain good data integrity.
The test was left to run for 12 hours.
[edit]
Results
- Senagent.exe is recorded as consistently pumping out close to 400 bytes of data every 2nd poll - that is, a peak of 400 bytes every 3 minutes approx. The intermediate poll shows zero or very close to zero bytes. I don't actually understand why there is this behaviour, but that is what the recorded data per poll shows.
- Data written from the Windows network card across the network shows a little different. Over the test period, data written remained constant (flat line) at 0.1Kb/sec - no peaks and no troughs. That is 100 bytes/sec - not much at all.
The above results yield the following information
- Up to 100 000 Windows hosts can be monitored on a single network segment before saturating a 100M network
- remember 100M network is capable of 10Mb/sec throughput.
- Conversely, given a more realistic 100 Windows hosts being monitored, the senagent information would account for only 10Kb/sec, or 0.1% of the capable network throughput on a 100M network
In short any concerns regarding the impact on the network by senagent.exe are unfounded. The impact is negligable.