COSserver Communications
This page was last modified 06:29, 13 April 2006.From Documentation
| Revision as of 03:19, 13 April 2006 Moff (Talk | contribs) (→General Security Issues) ← Previous diff |
Current revision Moff (Talk | contribs) (→PCgui Login) |
||
| Line 3: | Line 3: | ||
| === What is COSserver? === | === What is COSserver? === | ||
| - | COSserver is a TCP service listening on port 9002 by default. It performs three separate services for COSmanager applications. This document applies to COSmanager version 4.2.4 or later: | + | COSserver is a TCP service listening on port 9002 by default. It performs three separate services for COSmanager applications. This document applies to COSmanager version 4.2.4 or later, PCgui version 4.2.4 or later, and Enterprise Windows Client (EWC) version 3.1 or later: |
| - | #PCgui login; | + | #PCgui login |
| - | #Remote Unix/Linux GUI login; | + | #Remote Unix/Linux GUI login |
| - | #Remote command execution (from remote FSremote invocations); | + | #Remote command execution (from remote FSremote invocations). |
| It is possible that in future releases of COSmanager that it will be enhanced to perform more services. | It is possible that in future releases of COSmanager that it will be enhanced to perform more services. | ||
| + | <br> | ||
| === General Security Issues === | === General Security Issues === | ||
| Line 22: | Line 23: | ||
| Only one TCP port (9002) is used, meaning that Firewall configuration is simpler. | Only one TCP port (9002) is used, meaning that Firewall configuration is simpler. | ||
| - | If stronger security is required, then we recommend that the [[SSH_Communications]] method be used. Of course this requires more effort to setup (public/private keys must be generated on all hosts), and transmission of data may be slower. | + | If stronger security is required, then we recommend that the [[SSH Communications]] method be used. Of course this requires more effort to setup (public/private keys must be generated on all hosts), and transmission of data may be slower. |
| <br> | <br> | ||
| Line 29: | Line 30: | ||
| When a PCgui user logs into a host, it sends a request to the COSserver service on that host to: | When a PCgui user logs into a host, it sends a request to the COSserver service on that host to: | ||
| - | a) Authenticate the username and password; and | + | :*authenticate the username and password, and |
| - | b) Start the COSmanager application on that host. | + | :*start the COSmanager application on that host. |
| To perform the username authentication, the username and the encrypted password are sent from the PC to the COSserver process running on the server, where the authentication takes place, verifying the username and password against the Unix username and password. | To perform the username authentication, the username and the encrypted password are sent from the PC to the COSserver process running on the server, where the authentication takes place, verifying the username and password against the Unix username and password. | ||
| - | Assuming that authentication is successful, the requested COSmanager application is started, with the GUI_HOST & GUI_PORT environment variables set to the PC's IP address and PCgui's listening port respectively. The listening port is 9003 by default, but can be changed by reconfiguring PCgui. These two variables are used by the COSmanager GUI toolset as the destination to send all GUI display requests, which are interpreted by PCgui and then displayed on the PC's screen. | ||
| + | :[[Image:COSserver comms.png|alt text]] | ||
| + | |||
| + | |||
| + | Assuming that authentication is successful, the requested COSmanager application is started, with the <tt>GUI_HOST</tt> and <tt>GUI_PORT</tt> environment variables set to the PC's IP address and PCgui's listening port respectively. The listening port is 9003 by default, but can be changed by reconfiguring PCgui. These two variables are used by the COSmanager GUI toolset as the destination to send all GUI display requests, which are interpreted by PCgui and then displayed on the PC's screen. | ||
| + | |||
| + | <br> | ||
| === Remote COSmanager Command Execution === | === Remote COSmanager Command Execution === | ||
| Line 48: | Line 54: | ||
| Once the request has been authenticated, data sent or received is transmitted unencrypted over the same socket. This is a major advantage over Remote Shell (rsh) protocol which uses 2 sockets with port numbers in the range 512 to 1023. It also provides a much higher level of security. | Once the request has been authenticated, data sent or received is transmitted unencrypted over the same socket. This is a major advantage over Remote Shell (rsh) protocol which uses 2 sockets with port numbers in the range 512 to 1023. It also provides a much higher level of security. | ||
| + | <br> | ||
| === Remote Unix/Linux GUI Login === | === Remote Unix/Linux GUI Login === | ||
| This is invoked when a remote COSmanager GUI application or command is invoked from another COSmanager GUI application. This functions essentially in an identical way to the Remote COSmanager Command Execution, explained above, except that only a COSmanager GUI application can be started, not an arbitrary command. As with the PCgui, any fields in "prompt" forms that are invisible (eg: passwords) are transmitted encrypted. | This is invoked when a remote COSmanager GUI application or command is invoked from another COSmanager GUI application. This functions essentially in an identical way to the Remote COSmanager Command Execution, explained above, except that only a COSmanager GUI application can be started, not an arbitrary command. As with the PCgui, any fields in "prompt" forms that are invisible (eg: passwords) are transmitted encrypted. | ||
Current revision
Contents |
COSserver Communications
What is COSserver?
COSserver is a TCP service listening on port 9002 by default. It performs three separate services for COSmanager applications. This document applies to COSmanager version 4.2.4 or later, PCgui version 4.2.4 or later, and Enterprise Windows Client (EWC) version 3.1 or later:
- PCgui login
- Remote Unix/Linux GUI login
- Remote command execution (from remote FSremote invocations).
It is possible that in future releases of COSmanager that it will be enhanced to perform more services.
General Security Issues
COSserver generally receives and transmits data as unencrypted ASCII text. The exception to this is that passwords and any fields in COSmanager "prompt" forms which are invisible are transmitted encrypted. The encryption algorithm used is proprietary to Functional Software.
COSserver is more secure that using Remote Shell (rsh) and Remote Login (rlogin) because:
- passwords transmitted are encrypted
- the use of random numbers and encrypted hash codes to prevent IP spoofing.
Only one TCP port (9002) is used, meaning that Firewall configuration is simpler.
If stronger security is required, then we recommend that the SSH Communications method be used. Of course this requires more effort to setup (public/private keys must be generated on all hosts), and transmission of data may be slower.
PCgui Login
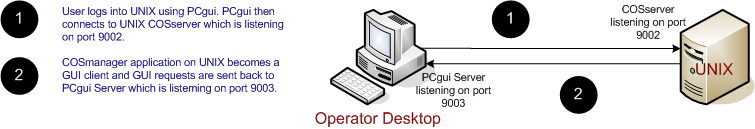
When a PCgui user logs into a host, it sends a request to the COSserver service on that host to:
- authenticate the username and password, and
- start the COSmanager application on that host.
To perform the username authentication, the username and the encrypted password are sent from the PC to the COSserver process running on the server, where the authentication takes place, verifying the username and password against the Unix username and password.
Assuming that authentication is successful, the requested COSmanager application is started, with the GUI_HOST and GUI_PORT environment variables set to the PC's IP address and PCgui's listening port respectively. The listening port is 9003 by default, but can be changed by reconfiguring PCgui. These two variables are used by the COSmanager GUI toolset as the destination to send all GUI display requests, which are interpreted by PCgui and then displayed on the PC's screen.
Remote COSmanager Command Execution
As far as security goes, this is the most sensitive function that COSserver performs because it processes requests that are able run commands as the "root" user. Hence COSserver does a series of extra authentication steps to ensure that the request is genuine. These are:
- The local HOSTINFO table is consulted, to ensure that the request originates from a known COSmanager host
- COSserver generates a random number, which is passed back to the host making the request. This random number is then hashed with the contents of the request, and the encrypted hash code is passed back to COSserver. COSserver then verifies that the hash code is correct.
This makes it virtually impossible for anyone sniffing the network to pretend to be a legitimate COSmanager application running a command (IP spoofing). No passwords are used in this authentication.
Once the request has been authenticated, data sent or received is transmitted unencrypted over the same socket. This is a major advantage over Remote Shell (rsh) protocol which uses 2 sockets with port numbers in the range 512 to 1023. It also provides a much higher level of security.
Remote Unix/Linux GUI Login
This is invoked when a remote COSmanager GUI application or command is invoked from another COSmanager GUI application. This functions essentially in an identical way to the Remote COSmanager Command Execution, explained above, except that only a COSmanager GUI application can be started, not an arbitrary command. As with the PCgui, any fields in "prompt" forms that are invisible (eg: passwords) are transmitted encrypted.